Block List Settings
The block list setting page list the conditions of how to define a blocked IP address. Modify the following settings to create the block list feature to meet your need.
[General]
Block list feature can be turned on or off, and adjust cache size.
When [Block Failed Username] is set on, the blocked failed-authentication user names will be added at [Blocked User Name] page.
When [Blocked Log] is set off, blocked activities will not be added to [Logs] > [Blocked Logs]
| Item | Default value | Explanation |
| On/Off | On | Set Block List feature on or off |
| Cache Size | 512 | |
| Block Failed Username | Off | If set to on, the IP addresses from which the SIP packets are sent with failed authentication user name will be added to Blocked IP Address database |
| Do not Block Local IP Address | On | If set to on, the packets from local IP addresses will not be blocked even the local IP addresses have been added to blocked IP Address database. |
| Email Alert
(v3.6 or later) |
On | If set to on, the emails are sent to Administrators when a new IP address meets the monitoring conditions and added to the blocked list. |
[Attempt Tracking/Monitoring]
You can adjust detection frequency for attacking attempts.
If the attacking attempts meet the tracking frequency setting in [Invalid Destination], [Invalid Packet], [Multiple Accesses] and [Prefix Scan] fields and are sent from the same IP address, this IP address will be added to [Blocked IP Address] page automatically.
The failed authentication user names will be added to [Blocked User Name] page automatically if the failed authentication attempts from different IP addresses are using the same failed authentication user name and meet the tracking frequency setting in the [Failed Authentication] field.
| Item | Default value | Explanation |
| Failed Authentication | 60 times in 259200 sec | The frequency of the failed authentication activities received from the same IP address that will be added as blocked IP address |
| Invalid Destination | 20 times in 30 sec | The frequency of SIP packets with invalid destination received from the same IP address that will be added as blocked IP address |
| Malformed Packet | 10 times in 10 sec | The frequency of sending invalid SIP packets received from the same IP address that will be added as blocked IP address |
| Multiple Accesses | 1000 times in 5 sec | The frequency to access from the same IP address that will be added as blocked IP address |
| Prefix Scan | 60 times in 60 sec | The frequency to prefix scan received from the same IP address that will be added as blocked IP address |
| Multiple Transport Connections
(v3.4 or later) |
20 times in 60 sec | The frequency of requests for transport layer connections received from the same IP address that will be added as blocked IP address |
[Notify to Other Brekeke SIP Servers] section
When this feature is set on, the blocked IP addresses in current Brekeke SIP Server [Blocked IP Address] page will be updated on the remote Brekeke SIP Server(s) located at IP(s) set in [IP addresses] field.
Multiple remote IP addresses or domanin name can be set in [IP addresses or FQDN] field, separated by comma, such as, 192.168.200.1,192.168.200.2.
The following Dial Plan rule is needed at remote Brekeke SIP Server to accept the blocked IP notification:
--------------------- [Matching Patterns] $request = ^MANAGEMENT $addr = <Brekeke_SIP_Server_IP> Command = (.+) [Deploy Patterns] $action = %1 ---------------------
Replace <Brekeke_SIP_Server_IP> with the Brekeke SIP Server IP address with [Notify to Other Brekeke SIP Servers] setup.
| Item | Default value | Explanation |
| On/Off | off | Enable or disable to send notify to other Brekeke SIP Server about blocked IP addresses |
| IP addresses or FQDN | IP addresses or FQDN of the remote Brekeke SIP Server where the NOTIFY will be sent
Multiple addresses or domain names can be set and separated by comma |
[Notify to HTTP Servers] section
When this feature is set on, the blocked(unblocked) IP addresses in current Brekeke SIP Server [Blocked IP Address] page will be notified to remote HTTP server.
Any URL can be set in both [URL (Block) (*1)] field and [URL (Unblock) (*1)] field.
| Item | Default value | Explanation |
| On/Off | off | Enable or disable to send notify to HTTP Server about blocked/unblocked IP addresses |
| URL (Block) (*1) | URL of the remote HTTP Server where the notification will be sent when an ip address becomes blocked | |
| URL (Unblock) (*1) | URL of the remote HTTP Server where the notification will be sent when an ip address becomes unblocked |
[Reverse Proxy] section
In the case a reverse proxy is located in front of the Brekeke SIP Server, in order to inform the actual source IP address to the Brekeke SIP Server, this settings are needed.
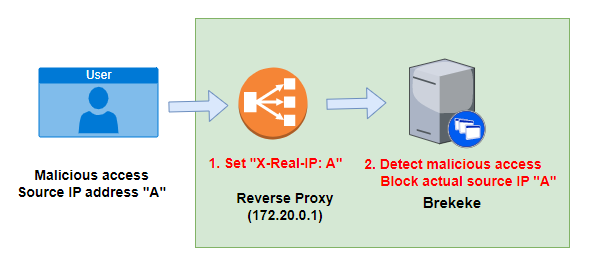
| Item | Default value | Explanation |
| Reverse Proxy IP address pattern | Set Reverse Proxy IP address pattern
Example: ^172\.20\.0\.1$ |
|
| HTTP header for remote IP address | Set HTTP header that includes actual source IP address
Example: X-Real-IP *The reverse proxy server needs to set an actual source ip address into the X-Real-IP header before the server forwards http requests. |
|
| HTTP Header pattern | If [HTTP Header pattern] is set, match the HTTP header values and use the first group (enclosed in parentheses) as the remote IP address.
If [HTTP Header pattern] is empty, use the entire HTTP header value as the remote IP address. |
